Seeds of Inception - Part 7
Tags: AWS Organizations CloudTrail S3 KMS IAMPart 7 Global CloudTrail - A practical example for auditing your AWS infrastructure

Hi, I’m Pipeline Pete and I welcome you to “AWS things you should know about but don’t”. In this lesson we’ll learn how to enable AWS CloudTrail at the AWS Organizations level so that you never have to think about setting it up again (or live with that perpetual niggling fear that someone has tampered with it inside your account).
Typically you’ll see AWS CloudTrail enabled within a single account and recording events into a local S3 Bucket. When it is done this way though, there is always a possibility that a rogue actor, with the right permissions, can tamper with it.
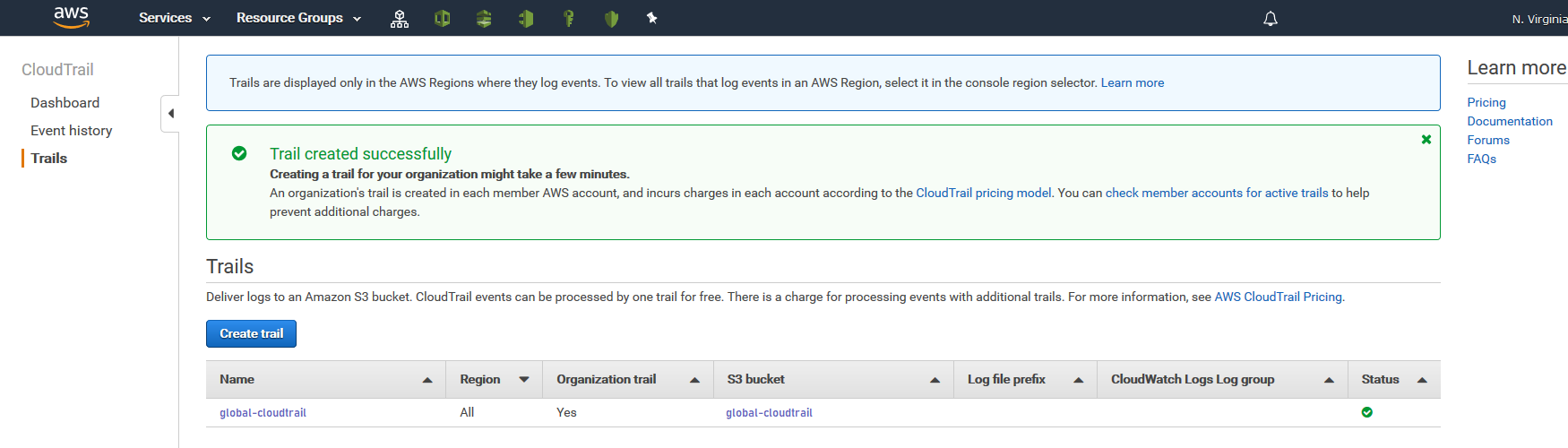
AWS CloudTrail can also be enabled through AWS Organizations. This means you can pick your Security/Audit account to receive ALL the trail events and the individual accounts don’t get a chance to tamper with them as they never see the trail. You even get the additional benefit that any new accounts that get added to your AWS Organizations automatically start recording events into the bucket.
When I asked around about this feature no one else knew about it! Big shout out to James Bromberger for pointing me in the right direction!
Prerequisites
These are the bits you’ll need before we get started:
- An AWS Account to host your AWS CloudTrail events. Typically, this is your Security/Audit account, but you can do all of this in the same account.
- AWS Organizations enabled on your account.
- An Inception Pipeline deployed into your Security/Audit account. We’ll cover this in the next section.
Deploying the pipeline
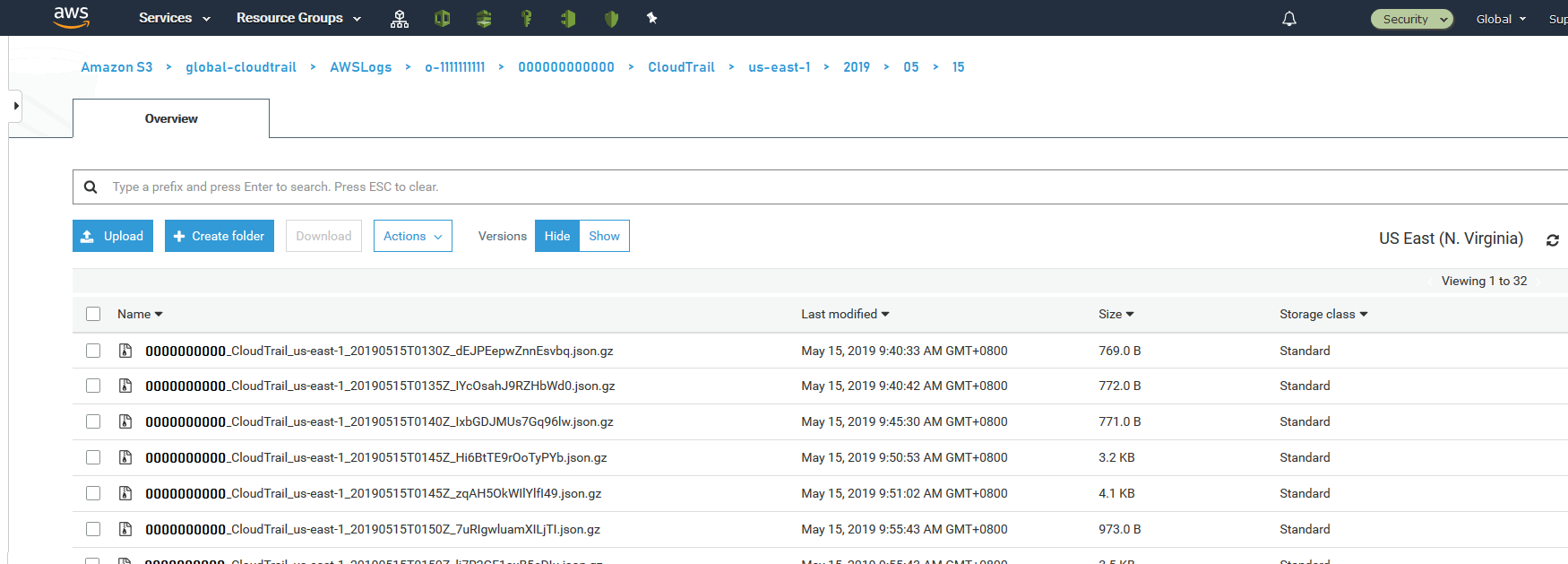
Before you can enable your Organizational CloudTrail you need to first deploy a couple of pieces of infrastructure. These are an S3 bucket to store the events in and a KMS key to protect them. To get you started I’ve prepared an Inception Pipeline for you to deploy. If you’ve never deployed one before, I highly recommend reading my original post - “Seeds of Inception - Seeding your Account with an Inception Pipeline”.
Warning! When AWS CloudTrail is enabled through AWS Organizations, it requires that the S3 bucket and KMS key reside in the North Virginia region. This means you must create the pipeline below in us-east-1, which I have already set for you in the init.sh script.
- Checkout the code from here.
- Change all the Inception Pipeline values in the
aws_seed.jsonandaws_seed-cli-parameters.jsonfiles to your specific values. See the original post if you need a refresher on how to do this. -
Open the
infrastructure/capability-global-cloudtrail.jsonand set the following values:Name Description ParamBucketPrefix A prefix for the bucket used to store the CloudTrail logs. A value of -cloudtrailis appended to this name to form the complete bucket name.ParamKmsKeyAlias A human friendly alias for the KMS key used to protect the files stored in S3. ParamMasterAccount The 12-digit AWS Account ID of your AWS Organizations master account. It is used to grant the appropriate levels of access between the accounts. ParamTransitionLogsToGlacierAfterThisManyDays To save on storage costs, move files older than this many days to Glacier storage. Defaults to 14 days. ParamExpireLogsFromGlacierAfterThisManyDays To save on storage costs, delete files older than this many days from Glacier. Defaults to approximately 6 months (180 days). -
Deploy the pipeline and wait for it to complete. Once it has you will need to extract the following values from the infrastructure stack. These will be used when configuring the CloudTrail trail in the next section:
Name Description BucketName The complete name of the S3 bucket where we are storing the logs. KmsKeyArn The KMS Key ARN to use to encrypt the logs.
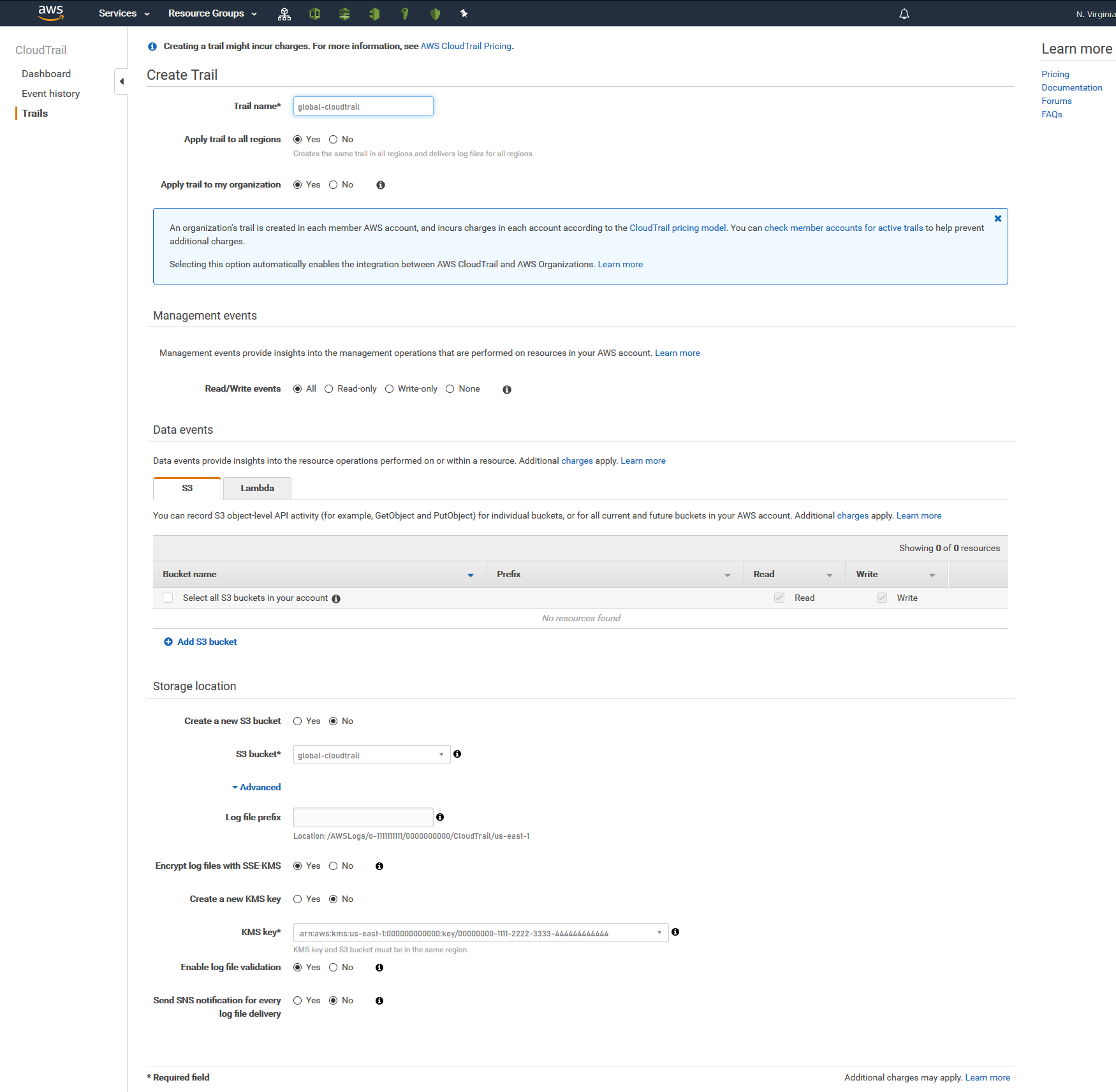
Enable AWS Organizations Global CloudTrail
Now that the underlying infrastructure is deployed, we can start on world domination configuring Global CloudTrail! Since this is a once-off activity it is easier and quicker to deploy via the console; one of the ultra-rare times that I will use the console for deployments.
Reminder I took hi-resolution images of each step. If you can’t make out what to do in each step, click the screenshot and it will open in a new tab.
"Upward and Onward"by Daniel Imfeld is licensed under CC BY-NC-SA 2.0